Safeguard staff to safeguard the organization from hackers

In December 2023, one of the largest insurance companies in the United States was the victim of a ransomware attack in which hackers obtained customer information.

Four years prior, the same company experienced a cybersecurity breach due to a vulnerability in a consumer data storage application. The aftermath was severe, with the company having to pay a $500,000 settlement with the Securities and Exchange Commission and a $1 million settlement to the New York Department of Financial Services. The financial and reputational damage was significant, and the full extent of the fallout from the recent attack is yet to be determined.
Such costly incidents, not just financially but to customer trust and confidence, have become all too commonplace.
In 2023, the ransomware industry saw an alarming 55.5% increase in victims worldwide over the previous year. Targets range from government and educational institutions to finance and health care providers — and everything in between. Any organization that holds personal and financial data on its clientele is at risk.
This makes insurance companies especially vulnerable. More insurers are taking proactive steps to combat would-be scammers and thieves, avoiding the most common vector of attack.
That used to be servers, but information technology departments have made substantial headway in hardening hardware against such assaults. Ever adaptable, hackers have found a better way to inflict their damage: Most ransomware is now delivered via phishing email. That is why addressing this vulnerability must be essential not after but before a cyber attack strikes.
Phishing for victims
Today’s phishing emails are a far cry from the clumsy old Nigerian prince offers or the “click here to update your password” scams, which were often riddled with spelling and grammar errors. These contemporary phishing attacks are powered by artificial intelligence and fueled by the vast amount of personal identifying information now easily accessible on all of your personnel, from the CEO to the claims adjuster hired last week. This increasing sophistication demands a constant update of your security measures.
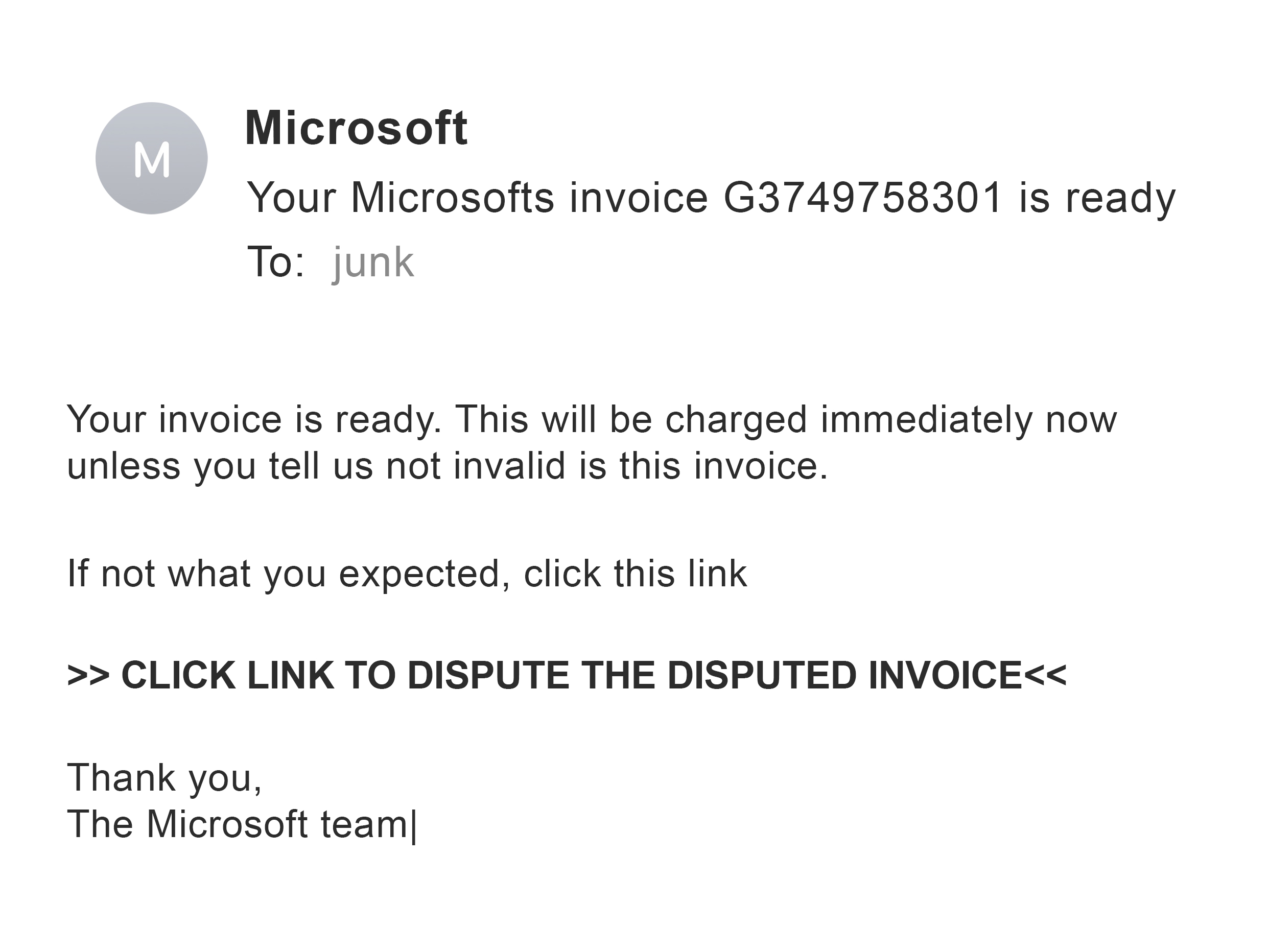
Regardless of the recipient, not many would be taken in by an email like this one:
But what about an email like this one?
At first glance, and even on close examination, it appears authentic because of a photo taken from social media and personal details acquired from multiple internet sources. One can understand how a recipient may be induced to click on a link. Once that happens, the hacker has won – he now has access to your organization’s IT systems. Hello ransomware, hello policyholder exposure, hello bad publicity, hello lawsuits.
A penetration test conducted at a financial organization found that emails such as this one routinely averaged a 4% click-through rate, with half of those also downloading a malicious payload. For a company with 50,000 employees, that is the potential for 2,000 successful breaches.
Protecting your organization from hackers
There isn’t much any organization can do to stop the creative ways thieves incorporate AI into their attacks. However, proactive enterprises can shut off their fuel supply by restricting access to personal data. Hackers are adept at their particular skill sets, but they are also lazy. With AI systems trained to avoid targets with incomplete data sets, hackers will always seek out the low-hanging fruit, which in this case are the companies where the most comprehensive profiles can be compiled.
Providing employees with a corporate account that monitors and eliminates the types of personal information that drive attacks can cost just a few dollars per employee per year. Some data privacy providers offer attractive licensing options and preventative solutions for large organizations. For example, such a strategy would replace authentic information (e.g., email addresses and phone numbers) with content that cannot be traced back to an individual user.
Education is equally essential. While every insurance organization likely provides some training on recognizing the common signatures of phishing emails and texts, a refresher may be necessary on the capabilities of AI-generated emails and how vigilance is now more important than ever.
Perhaps most critically, the industry as a whole must stop treating ransomware as an IT issue. This is a corporate challenge, and the conversation should be elevated to the C-suite with an eye toward asset protection and risk management.
Ransomware gangs have weaponized our home addresses, cell phone numbers, email addresses and other publicly accessible private content. To lower the risk of becoming a phishing victim, raise awareness of this uncomfortable truth with your employees and vendors. Forward-thinking companies should explore preventative and reactive measures as a new standard in strategic, data-compliant business operations.
Ron Zayas is CEO of IronWall360, an Incogni company. Contact him at [email protected].
© Entire contents copyright 2024 by InsuranceNewsNet.com Inc. All rights reserved. No part of this article may be reprinted without the expressed written consent from InsuranceNewsNet.com.







Lincoln’s Q1 earnings buffeted, as ‘strategic realignment’ progresses
Apollo riding big annuity sales, investment fees to strong financials
Advisor News
- LTC: A critical component of retirement planning
- Middle-class households face worsening cost pressures
- Metlife study finds less than half of US workforce holistically healthy
- Invigorating client relationships with AI coaching
- SEC: Get-rich-quick influencer Tai Lopez was running a Ponzi scam
More Advisor NewsAnnuity News
- Trademark Application for “EMPOWER MY WEALTH” Filed by Great-West Life & Annuity Insurance Company: Great-West Life & Annuity Insurance Company
- Conning says insurers’ success in 2026 will depend on ‘strategic adaptation’
- The structural rise of structured products
- How next-gen pricing tech can help insurers offer better annuity products
- Continental General Acquires Block of Life Insurance, Annuity and Health Policies from State Guaranty Associations
More Annuity NewsHealth/Employee Benefits News
- New Managed Care Study Findings Have Been Reported by G. Martin Reinhart and Co-Researchers (Psychiatric Medication Prescribing by Nurse Practitioners and Physician Associates for Medicare Beneficiaries): Managed Care
- Data on Managed Care Reported by Researchers at American Dental Association (Early association of expanded Medicare dental benefits to dentist billing in Medicare): Managed Care
- Researchers to study universal health care, as Coloradans face $1 billion in medical debt
- Veteran speaks out on veterans mail-order drug bill
- National Life Group Selects FINEOS AdminSuite to Transform Living Benefit and Life Insurance Claims Operations
More Health/Employee Benefits NewsLife Insurance News